I recently completed a project that tackles one often-overlooked security concern: stale IAM users. In large teams or long-running accounts, users get created and forgotten—posing a serious security risk.
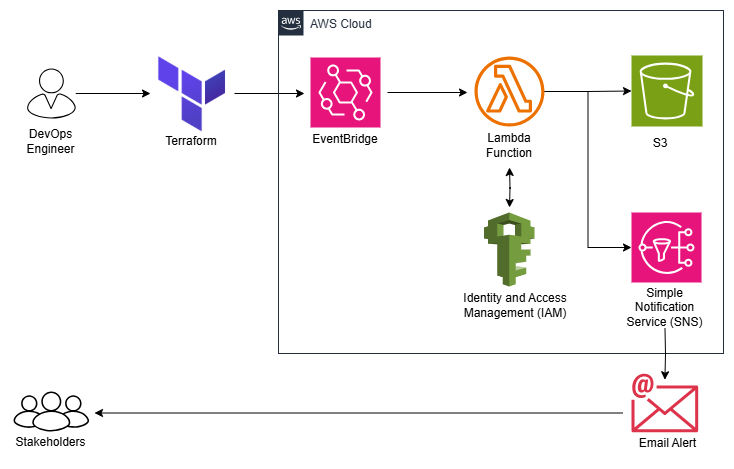
So I built an automation that detects IAM users inactive for 90+ days, notifies stakeholders via email, and archives reports in an S3 bucket. All of this is done serverlessly, and provisioned through Terraform.
Let me walk you through the stack.
What I Used
AWS Lambda (Python) – to run the logic
IAM – to fetch user activity data
Amazon EventBridge – to trigger the Lambda every Monday at 12PM
Amazon S3 – to store the generated reports
Amazon SNS – to send email alerts
Terraform – to deploy all the above
What It Does
Here’s how the system works:
Terraform provisions all necessary resources.
EventBridge schedules the Lambda to run weekly.
Lambda:
Fetches all IAM users.
Checks for users who haven’t logged in or changed passwords in the last 90 days.
Stores the list in an S3 bucket.
Publishes the list via SNS to stakeholders' emails.
The result? A fully automated security guardrail for IAM user hygiene.
Here’s the Repo on GitHub
Let’s connect on LinkedIn!